Introduction
In today’s digital age, where cyber threats are more prevalent than ever, implementing strong password policies is critical for safeguarding sensitive information. Passwords serve as the first line of defense against unauthorized access to systems and data. However, many organizations still struggle with weak passwords and poor password management practices, leaving them vulnerable to breaches and attacks.
The importance of implementing strong password policies cannot be overstated. A well-defined password policy not only protects your organization from cyber threats but also fosters a culture of security awareness among employees. When employees understand the significance of strong passwords, they are more likely to adhere to best practices and contribute to the overall security posture of the organization.
Throughout this blog post, we will explore various aspects of implementing strong password policies, including the key components that make up effective policies, secure password practices, and the role of training and awareness in fostering a security-conscious culture. We will also discuss the importance of monitoring compliance and having an incident response plan in place to address potential breaches.
As you read through this guide, you’ll discover actionable strategies for implementing strong password policies that can significantly reduce your organization’s risk of data breaches. By prioritizing password security, you not only protect your valuable data but also build trust with your clients and stakeholders.
Ultimately, implementing strong password policies is not just about creating rules; it’s about creating a mindset where every employee feels responsible for protecting sensitive information. This proactive approach to cybersecurity can make all the difference in today’s threat landscape. Let’s dive deeper into what it means to implement strong password policies and how you can effectively safeguard your organization against cyber threats.
What Does “Implementing Strong Password Policies” Entail?
When we talk about implementing strong password policies, we’re diving into a crucial aspect of cybersecurity that can make or break your organization’s defenses. In my years as a tech-savvy entrepreneur, I’ve seen firsthand how a solid password policy can prevent breaches that could cost companies millions. So, let’s unpack what this really means.
Understanding Strong Password Policies
At its core, implementing strong password policies means creating guidelines that dictate how passwords should be created, managed, and maintained within your organization. These policies are designed to enhance security by ensuring that passwords are robust enough to withstand attacks. Think of it like setting the rules for a game; without rules, chaos reigns.
For instance, I once worked with a startup that had no formal password policy. Employees used simple passwords like “123456” or “password.” It didn’t take long for hackers to exploit these weak credentials. After experiencing a breach, we learned the hard way that implementing strong password policies is not just beneficial—it’s essential.
Benefits of Strong Password Policies
So, why should you care about implementing strong password policies? Here are some key benefits:
- Reduced Risk of Breaches: The primary goal of these policies is to minimize the risk of unauthorized access. By requiring complex passwords and regular updates, you create multiple layers of defense against cyber threats.
- Increased Employee Awareness: When you establish clear guidelines for password creation and management, you foster a culture of security awareness among your employees. They become more vigilant and proactive in protecting sensitive information.
- Compliance with Regulations: Many industries have strict regulations regarding data protection. Implementing strong password policies helps ensure compliance with these regulations, avoiding potential fines and legal issues.
- Enhanced Reputation: A company known for its robust security measures will earn trust from clients and partners. This reputation can lead to increased business opportunities and customer loyalty.
Key Components of Strong Password Policies
Now that we understand the importance of implementing strong password policies, let’s look at some key components that should be included:
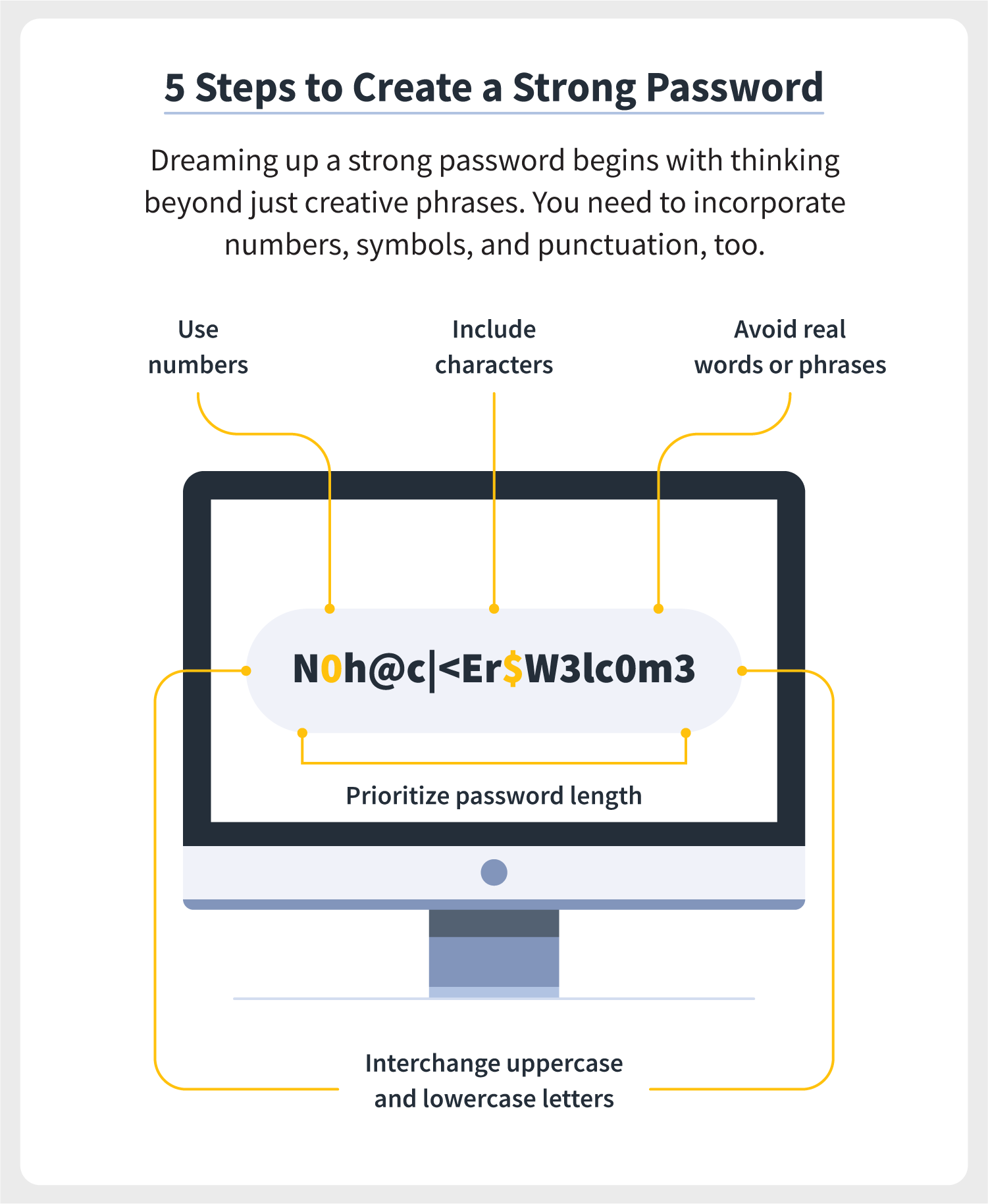
- Password Complexity Requirements: Require employees to create passwords that include a mix of uppercase letters, lowercase letters, numbers, and special characters. For example, instead of allowing “password123,” encourage something like “P@ssw0rd!23”.
- Length Matters: Set a minimum length for passwords—at least 12 characters is often recommended. Longer passwords are generally harder to crack.
- Regular Password Changes: Encourage or require employees to change their passwords regularly (every 60-90 days). This reduces the risk of old credentials being exploited.
- Account Lockout Mechanisms: Implement measures that lock accounts after a certain number of failed login attempts. This can deter brute-force attacks where hackers try multiple combinations rapidly.
Real-World Application
In my experience, the best way to implement these policies is through collaboration with your team. For example, during a company-wide meeting, I once shared statistics about data breaches linked to weak passwords. This sparked discussions about our current practices and led us to develop a comprehensive password policy together. We also decided to use an internal survey to gather feedback on our proposed policy changes. This not only made employees feel involved but also helped us identify potential challenges early on.
Implementing strong password policies is not just a checkbox on your security list; it’s an ongoing commitment to protecting your organization from cyber threats. By establishing clear guidelines and fostering a culture of security awareness, you can significantly reduce the risk of breaches and enhance your overall cybersecurity posture.
Why Are Password Management Strategies Essential?
As an experienced tech entrepreneur, I’ve learned that password management strategies are the backbone of any robust cybersecurity plan. These strategies encompass the processes and tools used to create, store, and manage passwords within an organization. Implementing effective password management practices is crucial for maintaining the integrity of your systems and protecting sensitive data.
Understanding Password Management Strategies
Password management strategies involve a set of guidelines and best practices that help organizations and individuals manage their passwords effectively. These strategies aim to ensure that passwords are strong, unique, and regularly updated, reducing the risk of unauthorized access and data breaches. One of the key components of password management strategies is the use of password managers. These tools securely store and encrypt passwords, making it easier for users to create and remember complex credentials. By using a password manager, employees can generate unique passwords for each account without the need to remember them all.
The Importance of Password Management Strategies
In today’s digital landscape, where cyber threats are constantly evolving, password management strategies have become increasingly important. Here are some reasons why:
- Reduced Risk of Data Breaches: Weak or reused passwords are a leading cause of data breaches. By implementing effective password management strategies, organizations can significantly reduce the risk of unauthorized access and protect their sensitive information.
- Improved Productivity: When employees struggle to remember multiple passwords, it can lead to productivity losses due to frequent password resets and login issues. Password management strategies streamline the login process, allowing employees to focus on their work.
- Compliance with Regulations: Many industries have strict regulations regarding data protection, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA). Implementing password management strategies helps organizations comply with these regulations and avoid potential fines and legal issues.
- Enhanced Reputation: Organizations that prioritize password security and implement effective management strategies are more likely to earn the trust of their clients and partners. This can lead to increased business opportunities and a stronger reputation in the industry.
The Impact of Password-Related Breaches
The consequences of password-related breaches can be severe for organizations. According to a study by the Ponemon Institute, the average cost of a data breach in 2021 was $4.24 million. These costs can include legal fees, regulatory fines, and the loss of customer trust. Moreover, password-related breaches can have long-lasting effects on an organization’s reputation. A study by the Ponemon Institute found that the average time to identify and contain a data breach is 287 days. During this time, organizations may face significant reputational damage and loss of business.
Implementing Password Management Strategies
Implementing effective password management strategies requires a multi-faceted approach. Here are some key steps to consider:
- Establish Password Policies: Create clear guidelines for password creation, storage, and management within your organization. These policies should include requirements for password complexity, length, and regular updates.
- Provide Employee Training: Educate your employees on the importance of password security and the best practices for creating and managing strong passwords. Regular training sessions can help reinforce these concepts and ensure that employees remain vigilant.
- Utilize Password Management Tools: Invest in a reliable password manager that can securely store and encrypt passwords. Ensure that the tool is compatible with your organization’s systems and provides features such as multi-factor authentication and secure password sharing.
- Monitor and Enforce Password Policies: Regularly monitor compliance with your password policies and enforce them when necessary. Use tools such as password auditing software to identify weak or reused passwords and take corrective action.
In today’s digital age, password management strategies are essential for maintaining the security and integrity of your organization’s systems and data. By implementing effective password policies, providing employee training, utilizing password management tools, and monitoring compliance, you can significantly reduce the risk of password-related breaches and protect your organization’s valuable assets.
How Can You Create Effective Password Policies?
Creating effective password policies is a critical step in implementing strong password policies within your organization. A well-crafted policy not only protects sensitive data but also fosters a culture of security awareness among employees. Here’s how you can develop and implement these policies effectively.
Key Components of Effective Password Policies
To create effective password policies, you need to consider several key components that will guide your organization in maintaining robust security practices. Here are the essential elements to include:
1. Password Complexity Requirements
One of the first steps in implementing strong password policies is to establish complexity requirements. Passwords should be a mix of:
- Uppercase letters
- Lowercase letters
- Numbers
- Special characters (e.g., @, #, $, %)
For example, instead of allowing simple passwords like “password123,” require employees to create something more complex, such as “S3cur3P@ssw0rd!.” This complexity makes it significantly harder for hackers to crack passwords through brute-force attacks.
2. Minimum Password Length
Setting a minimum password length is another critical aspect of effective password policies. Aim for passwords that are at least 12 characters long. Longer passwords are generally more secure because they provide more possible combinations for attackers to guess. In my experience, I’ve found that encouraging the use of passphrases—long strings of words or phrases—can also enhance security. For instance, “I_Love_Cybersecurity_2024!” is both memorable and complex.
3. Regular Password Changes
Another important element is requiring employees to change their passwords regularly. A common practice is to mandate password changes every 60 to 90 days. This practice helps mitigate the risk of old credentials being compromised. However, it’s essential to balance this with usability; frequent changes can lead to frustration and result in employees choosing weaker passwords or writing them down. Therefore, consider implementing a system that reminds users to change their passwords without being overly intrusive.

4. Account Lockout Mechanisms
Implementing account lockout mechanisms is a proactive way to protect against unauthorized access attempts. Set limits on failed login attempts (e.g., after five unsuccessful tries) and temporarily lock the account for a specified period (e.g., 15 minutes). This approach can deter brute-force attacks where hackers try numerous combinations rapidly.
Real-World Application: Crafting Your Policy
When I was tasked with developing a password policy for my team, I gathered input from various departments to ensure buy-in and practicality. We held brainstorming sessions where employees shared their experiences with password management challenges. This collaborative approach helped us create a policy that was not only effective but also user-friendly. We decided to use an online survey tool to gauge employee opinions on password length and complexity requirements before finalizing the policy. This feedback loop allowed us to address concerns and make adjustments based on real-world usage.
Communicating the Policy
Once your policy is drafted, communication is key. Make sure every employee understands the new guidelines and why they matter. Here are some effective ways to communicate your password policy:
- Kickoff Meeting: Host an all-hands meeting to introduce the new policy and explain its importance.
- Written Documentation: Provide clear, written guidelines that employees can refer back to as needed.
- Training Sessions: Conduct training sessions focused on creating strong passwords and recognizing phishing attempts.
- Regular Reminders: Use internal communication channels (like emails or newsletters) to remind employees about the importance of adhering to the policy.
Monitoring Compliance
Establishing a policy is just the beginning; you must also monitor compliance regularly. Use tools that can audit passwords across your organization, identifying weak or reused passwords that need attention. Regular audits will help ensure that everyone follows the guidelines and maintains strong security practices.
Creating effective password policies is a vital part of implementing strong password policies within your organization. By focusing on complexity requirements, minimum length, regular changes, and account lockout mechanisms, you can significantly enhance your cybersecurity posture. Remember, communication and training are crucial for ensuring compliance and fostering a culture of security awareness among your team.
What Secure Password Practices Should Be Adopted?
When it comes to implementing strong password policies, adopting secure password practices is just as crucial as creating the policies themselves. These practices empower employees to take an active role in safeguarding their accounts and sensitive information. Here’s a comprehensive look at some of the most effective secure password practices you should adopt within your organization.
Creating Strong Passphrases
One of the best secure password practices is to encourage employees to create strong passphrases instead of traditional passwords. A passphrase is a sequence of words or a sentence that is longer and often easier to remember. For example, instead of using “password123,” an employee could use “MyDogLovesToPlayFetch!”
Tips for Creating Strong Passphrases:
- Use a Mix of Words: Combine unrelated words to form a unique phrase. For instance, “BlueSky$Coffee!Dance” is both complex and memorable.
- Include Special Characters: Encourage the use of special characters and numbers within the passphrase. This adds an extra layer of security.
- Make It Personal: Suggest that employees incorporate personal interests or hobbies, which can help them remember their passphrases while still keeping them secure.
In my experience, I’ve found that when employees use passphrases, they are less likely to forget them, leading to fewer password reset requests.
Avoiding Common Pitfalls
While creating strong passwords is essential, it’s equally important to avoid common pitfalls that can compromise security. Here are some practices to steer clear of:
1. Don’t Use Personal Information
Many people make the mistake of using easily accessible personal information in their passwords, such as birthdays, names, or addresses. This information can often be found on social media or company websites, making it easier for attackers to guess passwords.For example, I once encountered an employee whose password was their child’s name followed by their birth year. It was simple enough for someone with malicious intent to figure out.
2. Avoid Dictionary Words
Using single dictionary words or common phrases makes passwords vulnerable to dictionary attacks, where attackers use software that systematically enters every word in the dictionary until they find a match. Instead, encourage employees to create unique combinations or phrases that are not easily guessable.
3. Don’t Reuse Passwords
Another common pitfall is reusing passwords across multiple accounts. If one account gets compromised, all other accounts using the same password are at risk. Implementing a policy that discourages password reuse is essential.
Utilizing Password Managers
Encouraging the use of password managers can significantly enhance secure password practices within your organization. These tools help employees generate and store complex passwords securely without needing to remember each one.
Benefits of Password Managers
- Secure Storage: Password managers encrypt stored passwords, making them accessible only to authorized users.
- Password Generation: They can generate strong, random passwords for each account, ensuring uniqueness and complexity.
- Ease of Use: Employees can easily log into multiple accounts without having to remember each password, reducing frustration and increasing productivity.
In my own experience, implementing a company-wide password manager transformed how our team approached password security. Employees felt empowered knowing they had a reliable tool at their disposal.
Implementing Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is another critical component of secure password practices. By requiring a second form of verification in addition to a password—such as a text message code or an authentication app—you add an extra layer of security.
Why 2FA Matters
- Enhanced Security: Even if a hacker manages to obtain a user’s password, they would still need the second factor to gain access.
- User Awareness: The implementation of 2FA raises awareness about security among employees, encouraging them to take their online safety seriously.
I recall rolling out 2FA in my organization after experiencing a phishing attempt targeting our email accounts. The added layer of security provided peace of mind and significantly reduced the likelihood of unauthorized access.
Regular Training and Awareness
Finally, regular training sessions on secure password practices are vital for reinforcing these concepts among employees. Here are some strategies for effective training:
- Interactive Workshops: Conduct workshops where employees can learn about creating strong passwords and recognizing phishing attempts.
- Quizzes and Challenges: Engage employees with quizzes or challenges related to password security; this can make learning fun and memorable.
- Regular Updates: Keep employees informed about new threats and best practices through newsletters or internal communication channels.
Adopting secure password practices is essential for successfully implementing strong password policies within your organization. By encouraging the creation of strong passphrases, avoiding common pitfalls, utilizing password managers, implementing two-factor authentication, and providing regular training, you empower your employees to take charge of their cybersecurity efforts.
How to Implement Password Management Tools?
In today’s digital landscape, where cybersecurity threats are constantly evolving, implementing password management tools is a crucial step in implementing strong password policies. These tools provide a secure and efficient way to store, manage, and share passwords within an organization. Here’s a comprehensive guide on how to implement password management tools effectively.
Understanding Password Management Tools
Password management tools are software applications designed to help individuals and organizations manage their login credentials securely. These tools typically offer features such as:
- Secure storage: Passwords are encrypted and stored in a secure vault, accessible only to authorized users.
- Password generation: The tools can generate strong, unique passwords for each account, reducing the risk of password reuse.
- Multi-factor authentication: Many password managers offer additional layers of security, such as biometric authentication or one-time codes.
- Secure sharing: Employees can securely share passwords with colleagues without exposing sensitive information.
Some popular password management tools include LastPass, 1Password, and Dashlane. Each tool has its own unique features and pricing models, so it’s essential to evaluate your organization’s needs before making a decision.
Benefits of Using Password Management Tools
Implementing password management tools offers numerous benefits for organizations looking to enhance their cybersecurity posture. Here are some of the key advantages:
- Improved security: By storing passwords securely and generating strong, unique credentials, password managers significantly reduce the risk of data breaches and unauthorized access.
- Increased productivity: Employees no longer need to remember multiple passwords, leading to fewer password reset requests and more efficient workflows.
- Centralized management: Password management tools allow administrators to monitor and control access to passwords, making it easier to enforce security policies and respond to incidents.
- Compliance with regulations: Many industries have strict regulations regarding data protection, such as GDPR or HIPAA. Password managers help organizations comply with these regulations by providing secure storage and access controls.
- Cost savings: Implementing password management tools can save organizations money in the long run by preventing costly data breaches and reducing the need for IT support related to password issues.
Steps to Implement Password Management Tools
Implementing password management tools within your organization requires careful planning and execution. Here are the key steps to follow:
- Evaluate your needs: Assess your organization’s specific requirements, such as the number of users, the types of accounts that need to be managed, and any industry-specific compliance requirements.
- Choose the right tool: Research and compare different password management tools based on your needs, features, and budget. Consider factors such as ease of use, integration with existing systems, and customer support.
- Develop a deployment plan: Create a detailed plan for deploying the password management tool, including timelines, communication strategies, and training resources.
- Communicate with employees: Inform employees about the new password management tool and its benefits, and provide clear instructions on how to use it.
- Provide training: Offer training sessions to help employees understand how to use the password management tool effectively and securely.
- Monitor and maintain: Regularly monitor the use of the password management tool and address any issues or concerns that arise. Keep the tool updated with the latest security patches and features.
Real-World Example
In my experience as a tech entrepreneur, I implemented a password management tool called LastPass to enhance our organization’s cybersecurity posture. We chose LastPass because it offered robust security features, easy integration with our existing systems, and competitive pricing. To ensure a smooth implementation, we developed a detailed deployment plan that included a phased rollout, communication strategies, and training resources.
We also designated a team of “password champions” who received advanced training and served as points of contact for their respective departments. The implementation of LastPass was a success, with employees quickly adapting to the new tool and appreciating the increased security and productivity benefits. We saw a significant reduction in password-related support requests, and our organization’s overall cybersecurity posture was strengthened.
Implementing password management tools is a critical step in implementing strong password policies within your organization. By providing secure storage, password generation, and centralized management, these tools help organizations enhance their cybersecurity posture and comply with industry regulations. By following a well-planned implementation process and providing ongoing training and support, organizations can ensure that password management tools are used effectively and securely.
What Role Does Two-Factor Authentication Play?
In the realm of cybersecurity, two-factor authentication (2FA) has emerged as a vital component of implementing strong password policies. By adding an extra layer of security beyond just a password, 2FA significantly enhances the protection of sensitive information and accounts. Let’s explore what 2FA is, why it matters, and how you can effectively implement it in your organization.
Understanding Two-Factor Authentication
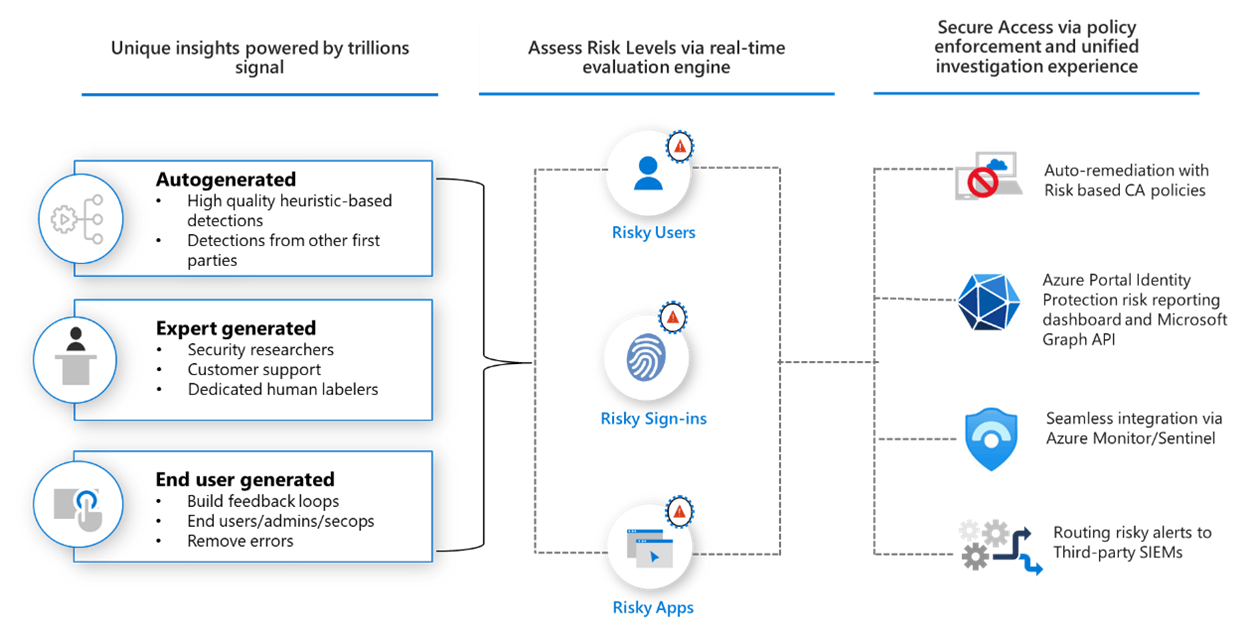
Two-factor authentication is a security process that requires two different forms of identification before granting access to an account. Typically, this involves something the user knows (like a password) and something the user has (like a smartphone or hardware token). For example, after entering their password, a user might receive a text message with a one-time code that they must enter to complete the login process. This additional step makes it much harder for unauthorized users to gain access, even if they have stolen or guessed the password.

Why Two-Factor Authentication Matters
Implementing 2FA is crucial for several reasons:
- Enhanced Security: The primary benefit of 2FA is its ability to provide an additional layer of security. Even if a hacker manages to obtain a user’s password through phishing or other means, they would still need the second factor to access the account. This drastically reduces the likelihood of unauthorized access.
- Mitigating Password Weaknesses: Many users still rely on weak or reused passwords, which can easily be compromised. By requiring 2FA, organizations can mitigate the risks associated with poor password practices.
- Building User Trust: When employees and customers see that an organization prioritizes security through measures like 2FA, it builds trust. Clients are more likely to engage with businesses that demonstrate a commitment to protecting their data.
- Compliance with Regulations: Many industries have regulations that mandate strong security measures for protecting sensitive information. Implementing 2FA can help organizations comply with these regulations and avoid potential fines.
Types of Two-Factor Authentication
There are several methods of implementing two-factor authentication, each with its own advantages:
- SMS-Based Verification: This is one of the most common forms of 2FA, where users receive a one-time code via text message after entering their password. While convenient, it’s worth noting that SMS can be vulnerable to interception.
- Authenticator Apps: Apps like Google Authenticator or Authy generate time-based one-time codes that users must enter after their password. These codes are more secure than SMS because they aren’t transmitted over potentially insecure channels.
- Email Verification: Some systems send a verification code to the user’s registered email address after they enter their password. While this adds a layer of security, it may not be as secure as other methods since email accounts can also be compromised.
- Hardware Tokens: Devices like YubiKeys provide physical tokens that users must insert into their computers or tap on their smartphones to authenticate. This method is highly secure but may require additional investment in hardware.
- Biometric Authentication: Using fingerprints or facial recognition offers a seamless and secure way to authenticate users without needing additional codes. Many smartphones now support biometric authentication for apps and services.
Implementing Two-Factor Authentication
To successfully implement two-factor authentication within your organization, follow these steps:
- Choose the Right Method: Evaluate the various 2FA methods and choose one that fits your organization’s needs and resources. For many businesses, using authenticator apps strikes a good balance between security and convenience.
- Communicate with Employees: Inform your employees about the upcoming implementation of 2FA and explain its importance in enhancing security. Clear communication helps alleviate any concerns about usability.
- Provide Training: Offer training sessions on how to set up and use 2FA effectively. Ensure employees understand how to troubleshoot common issues they might encounter during the setup process.
- Enforce Compliance: Make 2FA mandatory for all employees accessing sensitive systems or data. Regularly monitor compliance and provide support as needed.
- Review and Update Policies: As technology evolves, so do security threats. Regularly review your 2FA policies and update them as needed to adapt to new challenges.
Real-World Example
In my own experience implementing two-factor authentication at my company, we chose Google Authenticator due to its ease of use and strong security features. Before rolling it out company-wide, we conducted a pilot program with our IT department to iron out any issues. During training sessions, we emphasized real-world scenarios where 2FA could prevent unauthorized access—like if an employee’s credentials were compromised through phishing attacks. After implementing 2FA across our organization, we saw a dramatic decrease in unauthorized access attempts and increased employee awareness about cybersecurity threats.
Two-factor authentication plays an essential role in implementing strong password policies by providing an additional layer of protection against unauthorized access. By enhancing security, mitigating weaknesses in password practices, building user trust, and ensuring compliance with regulations, organizations can significantly improve their cybersecurity posture through effective implementation of 2FA.
How to Train Your Team on Secure Password Practices
Training your team on secure password practices is a vital step in implementing strong password policies. Even the most robust security measures can be undermined if employees are not aware of best practices or the importance of password security. Here’s how to effectively train your team to ensure they are equipped with the knowledge and skills to protect sensitive information.
The Importance of Training on Secure Password Practices
Investing time and resources into training your employees on secure password practices is essential for several reasons:
- Awareness of Threats: Employees who understand the risks associated with weak passwords are more likely to take security seriously. Training helps them recognize potential threats, such as phishing attacks or social engineering tactics.
- Empowerment: When employees are educated about secure password practices, they feel empowered to take responsibility for their own cybersecurity. This sense of ownership can lead to more vigilant behavior.
- Reduction in Security Incidents: Effective training can significantly reduce the number of security incidents related to weak passwords or poor practices. This not only protects sensitive information but also saves organizations time and money in the long run.
- Compliance with Regulations: Many industries require organizations to provide security training to their employees. By offering training on secure password practices, you help ensure compliance with these regulations.
Key Topics to Cover in Training Sessions
When planning your training sessions, consider including the following key topics:
1. Understanding Password Security
Start by explaining the importance of strong passwords and the role they play in overall cybersecurity. Discuss common threats, such as hacking, phishing, and credential stuffing, and how weak passwords can lead to data breaches.
2. Creating Strong Passwords
Teach employees how to create strong passwords by following best practices:
- Use a mix of uppercase letters, lowercase letters, numbers, and special characters.
- Avoid using personal information or easily guessable words.
- Encourage the use of passphrases for added security.
3. Password Management Tools
Introduce employees to password management tools that can simplify the process of creating and storing strong passwords. Provide demonstrations on how to use these tools effectively and securely.
4. Recognizing Phishing Attempts
Educate employees on how to identify phishing attempts that may compromise their credentials. Provide examples of common phishing emails and tactics, emphasizing the importance of verifying the source before clicking links or entering information.
5. The Importance of Two-Factor Authentication
Discuss the role of two-factor authentication (2FA) in enhancing security. Explain how it works and encourage employees to enable 2FA on their accounts whenever possible.
Effective Training Methods
To ensure that your training sessions are engaging and effective, consider using a variety of methods:
- Interactive Workshops: Conduct interactive workshops where employees can participate in discussions and hands-on activities related to password security. This approach encourages engagement and allows for real-time questions and feedback.
- E-Learning Modules: Create e-learning modules that employees can complete at their own pace. These modules can include quizzes and assessments to reinforce learning and track progress.
- Regular Refreshers: Cybersecurity is an ever-evolving field, so it’s essential to provide regular refresher courses on secure password practices. Schedule periodic training sessions to keep employees updated on new threats and best practices.
- Gamification: Incorporate gamification elements into your training sessions by creating challenges or competitions related to password security. This approach can make learning fun while reinforcing important concepts.
Real-World Example
In my experience implementing a training program focused on secure password practices, we organized a series of interactive workshops for our employees. We invited a cybersecurity expert to present real-life case studies involving data breaches caused by weak passwords. During these sessions, we conducted group activities where teams had to identify weak passwords from a list and suggest improvements. This hands-on approach not only made the training more engaging but also helped reinforce the importance of strong passwords in a memorable way.
Additionally, we followed up with e-learning modules that allowed employees to revisit key concepts at their convenience. After implementing this comprehensive training program, we saw a noticeable increase in employee awareness regarding password security, leading to fewer incidents related to compromised accounts.
Training your team on secure password practices is essential for successfully implementing strong password policies within your organization. By covering key topics such as understanding password security, creating strong passwords, recognizing phishing attempts, and utilizing password management tools, you empower your employees to take an active role in protecting sensitive information. Using a combination of interactive workshops, e-learning modules, regular refreshers, and gamification can make your training sessions engaging and effective. By investing in employee education, you foster a culture of security awareness that will benefit your organization as a whole.
How to Monitor and Enforce Password Policies
Monitoring and enforcing password policies is a critical aspect of implementing strong password policies within an organization. Even with comprehensive training and the use of password management tools, it’s essential to regularly monitor compliance and enforce policies to maintain a robust cybersecurity posture. Here’s how to effectively monitor and enforce password policies in your organization.
Monitoring Password Policy Compliance
Regularly monitoring compliance with your password policies is crucial for identifying potential vulnerabilities and ensuring that employees adhere to best practices. Here are some strategies for effective monitoring:
- Password Auditing Tools: Utilize password auditing software that can scan your network and identify weak, reused, or compromised passwords. These tools can provide detailed reports on policy compliance and highlight areas that need attention.
- Regular Password Checks: Conduct periodic password checks, either manually or through automated tools, to assess the strength and uniqueness of employee passwords. This can help identify potential weak spots before they can be exploited by attackers.
- Monitoring Login Attempts: Monitor login attempts across your organization to detect suspicious activity, such as multiple failed login attempts or logins from unusual locations. This can help identify potential breaches or unauthorized access attempts.
- Incident Response Monitoring: Closely monitor your incident response plan and procedures to ensure that they are effective and up-to-date. In the event of a breach, it’s crucial to have a well-defined process for responding and mitigating the impact.
Enforcing Password Policies
Enforcing password policies is essential for ensuring that employees adhere to best practices and maintain a strong cybersecurity posture. Here are some strategies for effective enforcement:
- Clear Communication: Clearly communicate your password policies to all employees and ensure that everyone understands the importance of compliance. Provide regular reminders and updates to keep the policies top-of-mind.
- Consequences for Non-Compliance: Establish clear consequences for non-compliance with password policies, such as disciplinary action or restricted access to sensitive systems. Consistently apply these consequences to maintain the effectiveness of your policies.
- Automated Enforcement: Utilize password management tools and other security software to automatically enforce password policies. For example, you can set minimum password length and complexity requirements, or automatically lock accounts after a certain number of failed login attempts.
- Regular Policy Reviews: Regularly review and update your password policies to ensure that they remain effective in the face of evolving threats and changing business needs. Involve key stakeholders, such as IT, security, and compliance teams, in the review process to ensure that all perspectives are considered.
Real-World Example
In my experience as a tech entrepreneur, we implemented a comprehensive password policy that included regular monitoring and enforcement measures. We utilized a password auditing tool called PassPack to regularly scan our network and identify potential vulnerabilities. To enforce the policy, we required all employees to use a password manager called LastPass to generate and store strong, unique passwords.
We also implemented two-factor authentication for all accounts to add an extra layer of security. To monitor compliance, we set up automated alerts to notify us of any suspicious login activity or failed attempts. We also conducted regular password checks, either through the password manager or by manually reviewing a sample of employee passwords.
When we identified instances of non-compliance, such as employees using weak or reused passwords, we took immediate action. We provided additional training and support to help employees understand the importance of strong password practices. In cases of repeated non-compliance, we escalated the issue to management for further action.
By implementing a combination of monitoring and enforcement strategies, we were able to maintain a strong cybersecurity posture and protect our organization from potential breaches. Regular reviews and updates to our password policy ensured that it remained effective in the face of evolving threats.
What Should Be Included in an Incident Response Plan?
When it comes to implementing strong password policies, having a comprehensive incident response plan in place is crucial. An incident response plan outlines the steps an organization should take in the event of a security breach or other cybersecurity incident. By having a well-defined plan, organizations can minimize the impact of an incident and quickly restore normal operations. Here’s what should be included in an effective incident response plan for password-related incidents.
Understanding the Importance of Incident Response Plans
In today’s digital landscape, where cyber threats are constantly evolving, it’s not a matter of if a security breach will occur, but when. Password-related incidents, such as credential stuffing attacks or phishing scams, can lead to significant data breaches and financial losses if not properly managed.
An incident response plan helps organizations prepare for and respond to these incidents effectively. By outlining clear procedures and responsibilities, an incident response plan ensures that everyone knows what to do in the event of a breach, reducing confusion and minimizing the impact on the organization.
Key Components of an Incident Response Plan
An effective incident response plan for implementing strong password policies should include the following key components:
- Incident Identification and Classification: The plan should clearly define what constitutes a security incident and how to classify its severity. This helps ensure that the appropriate response measures are taken based on the nature and scope of the incident.
- Incident Response Team: Identify the members of the incident response team, including their roles and responsibilities. This team should include representatives from various departments, such as IT, security, legal, and communications.
- Incident Response Procedures: Outline the specific steps to be taken in response to a security incident. This should include procedures for containing the breach, investigating the cause, and restoring normal operations.
- Communication Plan: Establish a communication plan that outlines how to communicate with internal and external stakeholders, such as employees, customers, and regulatory authorities. The plan should include templates for various types of communications, such as breach notifications and press releases.
- Recovery and Restoration: Develop a plan for recovering from a security incident and restoring normal operations. This should include procedures for restoring data from backups, rebuilding systems, and verifying the integrity of restored data.
- Lessons Learned: After an incident has been resolved, conduct a post-incident review to identify areas for improvement. This should include an analysis of the incident, the effectiveness of the response measures, and any lessons learned that can be applied to future incidents.
Real-World Example: Responding to a Password Breach
In my experience as a tech entrepreneur, we once experienced a password breach that compromised the accounts of several employees. As soon as we became aware of the incident, we immediately activated our incident response plan. First, we classified the incident as a high-severity breach due to the sensitive nature of the compromised data. We then assembled our incident response team, which included representatives from IT, security, legal, and communications.
The incident response team immediately took steps to contain the breach, including resetting all compromised passwords and implementing two-factor authentication for all accounts. We also conducted a thorough investigation to determine the cause of the breach and identify any additional vulnerabilities. As part of our communication plan, we promptly notified affected employees and provided guidance on how to secure their accounts. We also communicated with regulatory authorities and external stakeholders, such as customers and partners, to ensure transparency and maintain trust.
After the incident was resolved, we conducted a post-incident review to identify areas for improvement. We found that while our strong password policies were effective in preventing many types of attacks, we needed to enhance our training and awareness programs to better prepare employees for phishing scams. We also identified the need for more robust monitoring and enforcement measures to ensure compliance with our password policies. By implementing these improvements, we were able to strengthen our overall cybersecurity posture and reduce the risk of future incidents.
Having a well-defined incident response plan is essential for implementing strong password policies and protecting an organization from the devastating effects of a security breach. By including key components such as incident identification, response procedures, communication plans, and lessons learned, organizations can minimize the impact of a password-related incident and quickly restore normal operations. Regular testing and updating of the incident response plan is crucial to ensure that it remains effective in the face of evolving threats and changing business needs. By prioritizing incident response planning, organizations can demonstrate their commitment to cybersecurity and maintain the trust of their customers and stakeholders.
How Can You Foster a Culture of Security Awareness?
Fostering a culture of security awareness is essential for successfully implementing strong password policies within your organization. A security-aware culture encourages employees to prioritize cybersecurity in their daily activities, making them more vigilant and proactive in protecting sensitive information. Here’s how you can create and nurture this culture effectively.
The Importance of Security Awareness
Creating a culture of security awareness is vital for several reasons:
- Employee Engagement: When employees understand the importance of cybersecurity, they are more likely to engage with security practices, including adhering to strong password policies. This engagement can lead to better compliance and fewer security incidents.
- Reduction in Human Error: Many security breaches occur due to human error, such as falling for phishing scams or using weak passwords. By fostering a culture of awareness, you can reduce these errors and improve overall security.
- Empowerment: Employees who are educated about cybersecurity feel empowered to take action when they notice suspicious activity or potential threats. This proactive behavior can significantly enhance your organization’s security posture.
- Compliance: Many industries have regulations that require organizations to provide cybersecurity training and promote awareness among employees. Fostering a culture of security awareness helps ensure compliance with these regulations.
Strategies for Fostering Security Awareness
To foster a culture of security awareness that supports implementing strong password policies, consider the following strategies:
1. Regular Training and Workshops
Conduct regular training sessions and workshops focused on cybersecurity best practices, including the importance of strong passwords. These sessions should cover topics such as:
- Creating strong passwords
- Recognizing phishing attempts
- Understanding the consequences of weak passwords
In my experience, interactive workshops that include real-life scenarios and hands-on activities tend to be the most effective. Employees are more likely to remember the information when they can actively participate in discussions and exercises.
2. Create Clear Policies and Guidelines
Ensure that your organization has clear policies regarding password management and cybersecurity practices. These policies should be easily accessible and regularly updated to reflect current best practices. When employees understand the expectations set forth in your strong password policies, they are more likely to comply with them. Consider using infographics or quick reference guides that summarize key points for easy reference.
3. Use Gamification Techniques
Gamification can be an effective way to engage employees in learning about cybersecurity. Consider implementing challenges or competitions related to password security, where employees can earn rewards for demonstrating their knowledge and adherence to strong password policies. For example, you could create a quiz on password best practices, offering prizes for those who score the highest or show significant improvement over time. This approach not only makes learning fun but also reinforces the importance of secure password practices.
4. Encourage Open Communication
Foster an environment where employees feel comfortable discussing cybersecurity concerns or reporting suspicious activity without fear of repercussions. Encourage open communication about potential threats and share success stories where vigilance led to preventing a breach. Regularly remind employees that they play a crucial role in protecting the organization by adhering to strong password policies and being vigilant about security threats.
5. Recognize and Reward Good Practices
Recognizing employees who consistently follow strong password policies and demonstrate good cybersecurity practices can reinforce positive behavior throughout your organization. Consider implementing a recognition program that highlights individuals or teams who excel in maintaining security standards. For instance, you could feature “Security Champions” in company newsletters or hold monthly meetings where you celebrate those who have made significant contributions to fostering a culture of security awareness.
Real-World Example
In my own experience, I implemented a comprehensive training program aimed at fostering a culture of security awareness within my organization. We began by conducting an initial assessment to identify knowledge gaps related to password management and overall cybersecurity practices.
Based on this assessment, we developed a series of engaging workshops focused on the importance of creating strong passwords, recognizing phishing attempts, and understanding our organization’s specific strong password policies. We also introduced gamification elements by hosting quarterly competitions where teams could compete against each other in solving cybersecurity-related challenges.
The winning team received recognition during our all-hands meetings, which helped motivate others to participate actively in training sessions. Over time, we saw a noticeable improvement in employee engagement with our security initiatives. Employees became more proactive in reporting suspicious activity and adhering to our strong password policies, ultimately reducing the number of incidents related to weak passwords or poor practices.
Fostering a culture of security awareness is essential for successfully implementing strong password policies within your organization. By providing regular training, creating clear policies, utilizing gamification techniques, encouraging open communication, and recognizing good practices, you empower employees to take an active role in protecting sensitive information. A strong culture of security awareness not only enhances compliance with password policies but also builds resilience against evolving cyber threats. By prioritizing security awareness, organizations can significantly improve their overall cybersecurity posture while safeguarding their valuable assets.
Final Thoughts: Building a Stronger Security Posture Through Password Policies
In an era where cyber threats are increasingly sophisticated, implementing strong password policies is not just a best practice; it’s a necessity. Organizations that prioritize password security significantly reduce their risk of data breaches and cyberattacks. By fostering a culture of security awareness and ensuring that employees understand the importance of adhering to these policies, you can create a robust defense against potential threats.
The Foundation of Strong Password Policies
The foundation of effective cybersecurity lies in implementing strong password policies that are clear, comprehensive, and accessible to all employees. These policies should encompass guidelines for creating strong passwords, regular updates, and the use of password management tools. By establishing these guidelines, organizations empower employees to take ownership of their security practices. Moreover, the integration of two-factor authentication (2FA) as part of your strong password policies adds an additional layer of protection. This multi-faceted approach ensures that even if a password is compromised, unauthorized access remains difficult.
Training and Awareness
As we’ve discussed throughout this blog post, training plays a crucial role in implementing strong password policies. Regular training sessions that focus on password security, recognizing phishing attempts, and understanding the consequences of weak passwords are essential for keeping cybersecurity at the forefront of employees’ minds.
By fostering a culture of security awareness, organizations can encourage employees to actively engage in protecting sensitive information. This proactive approach not only helps in compliance with regulations but also builds trust among clients and stakeholders.
Monitoring and Enforcement
Monitoring compliance with your strong password policies is vital for maintaining a secure environment. Utilizing password auditing tools to identify weak or reused passwords allows organizations to take corrective actions before breaches occur. Additionally, enforcing consequences for non-compliance reinforces the seriousness of adhering to these policies. Establishing regular reviews and updates to your password policies ensures they remain relevant in the face of evolving threats. This adaptability is key to maintaining a strong security posture over time.
Incident Response Preparedness
Even with the best strong password policies in place, incidents can still occur. Having a well-defined incident response plan ensures that your organization is prepared to handle breaches effectively. This plan should outline clear procedures for identifying incidents, containing breaches, and communicating with stakeholders. Conducting post-incident reviews allows organizations to learn from experiences and improve their strong password policies moving forward. Continuous improvement is essential for staying ahead of cyber threats.
In conclusion, building a stronger security posture through implementing strong password policies is an ongoing commitment that requires the involvement of every employee within your organization. By establishing clear guidelines, providing regular training, monitoring compliance, and preparing for potential incidents, you create a resilient defense against cyber threats. As technology continues to evolve, so too must your approach to cybersecurity. By prioritizing strong password practices and fostering a culture of security awareness, organizations can significantly mitigate risks and protect their most valuable assets—data and trust.
Frequently Asked Questions (F.A.Q.s)
- What are strong password policies?
Strong password policies are guidelines that dictate how passwords should be created, managed, and maintained to enhance security and protect sensitive information. - Why is implementing strong password policies important?
Implementing strong password policies is crucial to reduce the risk of unauthorized access, data breaches, and cyberattacks, thereby safeguarding organizational assets. - What are some key components of strong password policies?
Key components include password complexity requirements, minimum length, regular password changes, account lockout mechanisms, and the use of password managers. - How often should passwords be changed according to best practices?
Best practices recommend changing passwords every 60 to 90 days to minimize the risk of compromised credentials being exploited. - What are secure password practices employees should follow?
Employees should create complex passwords, avoid using personal information, refrain from reusing passwords across accounts, and utilize password managers. - How does two-factor authentication enhance password security?
Two-factor authentication adds an extra layer of security by requiring a second form of verification (e.g., a code sent to a mobile device) in addition to a password. - What tools can help enforce strong password policies?
Password management tools like LastPass or 1Password can help enforce strong password policies by securely storing passwords and generating complex credentials. - How can organizations train employees on secure password practices?
Organizations can conduct regular training sessions, workshops, and e-learning modules focused on creating strong passwords and recognizing phishing attempts. - What steps should be taken if a password breach occurs?
If a breach occurs, organizations should immediately reset compromised passwords, investigate the cause, notify affected users, and review security policies. - How can I foster a culture of security awareness in my organization?
Foster a culture of security awareness by providing ongoing training, promoting open communication about threats, recognizing good practices, and enforcing compliance with strong password policies.



